| 
Server Load Balancing Example
This is meant to be an example, and not a complete load balancing configuration.
Network Diagram
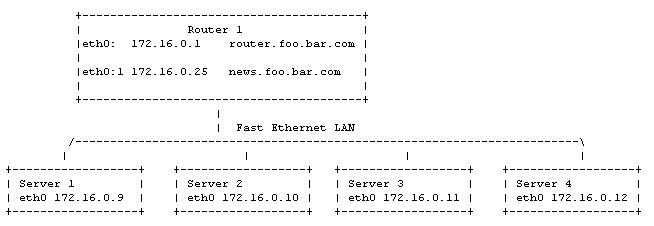
Ensure that the routers running the 4.0 distribution or later. Remember to save your configurations to flash whenever you are finished configuring your dynamic routing setup! To configure server load balancing , do the following:
1. At the Login: prompt, enter root.
2. At the Password: prompt, enter your password.
3. Choose Option 1 (Configuration and Update Menu) from the Main Menu. Select Option 3 (Service Configuration).
4. From the Service Configuration menu, you can see the status of the Firewall (IPtables) package. If IPtables is running, the option will show "(instated)".
5. To start IPtables, choose Option 2 (firewall) and choose Option 2 (Instate firewall rules) from the firewall menu.
Ensure you have configured IPtables prior to instating it.
In our example above, we will be configuring "Router 1" to load balance incoming news sessions. From the Firewall menu, choose Option 1 (Configure firewall rules). This will open a file in your default editor.
1. Move to the section of the file where you wish to insert the rule
2. Enter a header (in comments) that discribes the rule you are adding
3. Add the load balancing rule
The completed file for our example should look like this:
#!/bin/sh
################################################################################
# This is just iptables, if you need help see: #
# http://www.BoingWorld.com/workshops/linux/iptables-tutorial/ #
################################################################################
IPTABLES=/bin/iptables
echo -n "Setting up firewalling rules..."
################################################################################
# Flushing all rules. #
################################################################################
${IPTABLES} -P INPUT ACCEPT
${IPTABLES} -F INPUT
${IPTABLES} -P OUTPUT ACCEPT
${IPTABLES} -F OUTPUT
${IPTABLES} -P FORWARD ACCEPT
${IPTABLES} -F FORWARD
${IPTABLES} -F firewall
${IPTABLES} -t nat -F
${IPTABLES} -t mangle -F
################################################################################
# Setup All of the Nat Rules #
################################################################################
# Source Nat to the internet
${IPTABLES} -t nat -A POSTROUTING -o Serial0 -j SNAT --to 205.159.243.241
# Forward smtp to Server1 for the local email.
${IPTABLES} -t nat -A PREROUTING -i Serial0 -p TCP --dport smtp -j DNAT \
--to-destination 172.16.0.9:25
#
# Load Balancing
#
# Load Balance incomming nntp sessions by redirecting to local news servers.
# Local news servers: Server1 - Server4. IP addr: 172.168.0.9 - 172.16.0.12
${IPTABLES} -t nat -A PREROUTING -d 172.16.0.25 -p TCP --dport nntp -j DNAT \
--to-dest 172.16.0.9-172.16.0.12
################################################################################
# End Nat Rules #
################################################################################
################################################################################
# Setup the Firewall Rules #
################################################################################
# create the firewall chain
${IPTABLES} -N firewall
# lets accept stuff from trusted hosts and networks
${IPTABLES} -A firewall -i Serial0 -s 205.159.243.0/24 -j ACCEPT
${IPTABLES} -A firewall -i Serial0 -s 172.20.0.0/16 -j ACCEPT
# Here is where we start dropping packets that we don't want...
# For each portforward we will have a matching drop rule. If you want let a
# machine use one of the portforwards in general you should add it to the
# trusted list above.
${IPTABLES} -A firewall -i Serial0.1 -d 192.168.100.1 -p tcp --dport smtp -j DROP
# We will now make every packet in the Input and Forward chains jump to the
# Firewall chain
${IPTABLES} -A INPUT -j firewall
${IPTABLES} -A FORWARD -j firewall
###############################################################################
# End Firewall Rules #
###############################################################################
echo "done."
Remember to save your configurations to flash whenever you are finished configuring your dynamic routing setup! |